Security Policies
Security Policies describe under what situations certain actions will take place. They are designed to be powerful, with flexible matching rules on user sessions and traffic destinations. They support a diverse range of actions to give you the precise control over your users' traffic. For instance:
- Allow access to a privately hosted app.
- Block all user traffic to phishing sites.
- Act as an MITM, inspecting traffic to all privately hosted apps.
- Trigger self-approval workflow for sales people accessing GitHub.
In Security Policies, any deny rules takes precedence over run workflow and permit rules, and workflows also take precedence over permits. For example, given a policy that permits access to a site and a second policy that denies access for certain users to that site, the specified users would be subject to the second, blocking policy. Also, policies for higher order resources (e.g., subdomain.exampledomain.com) take precedence over those for lower order resources (e.g., exampledomain.com).
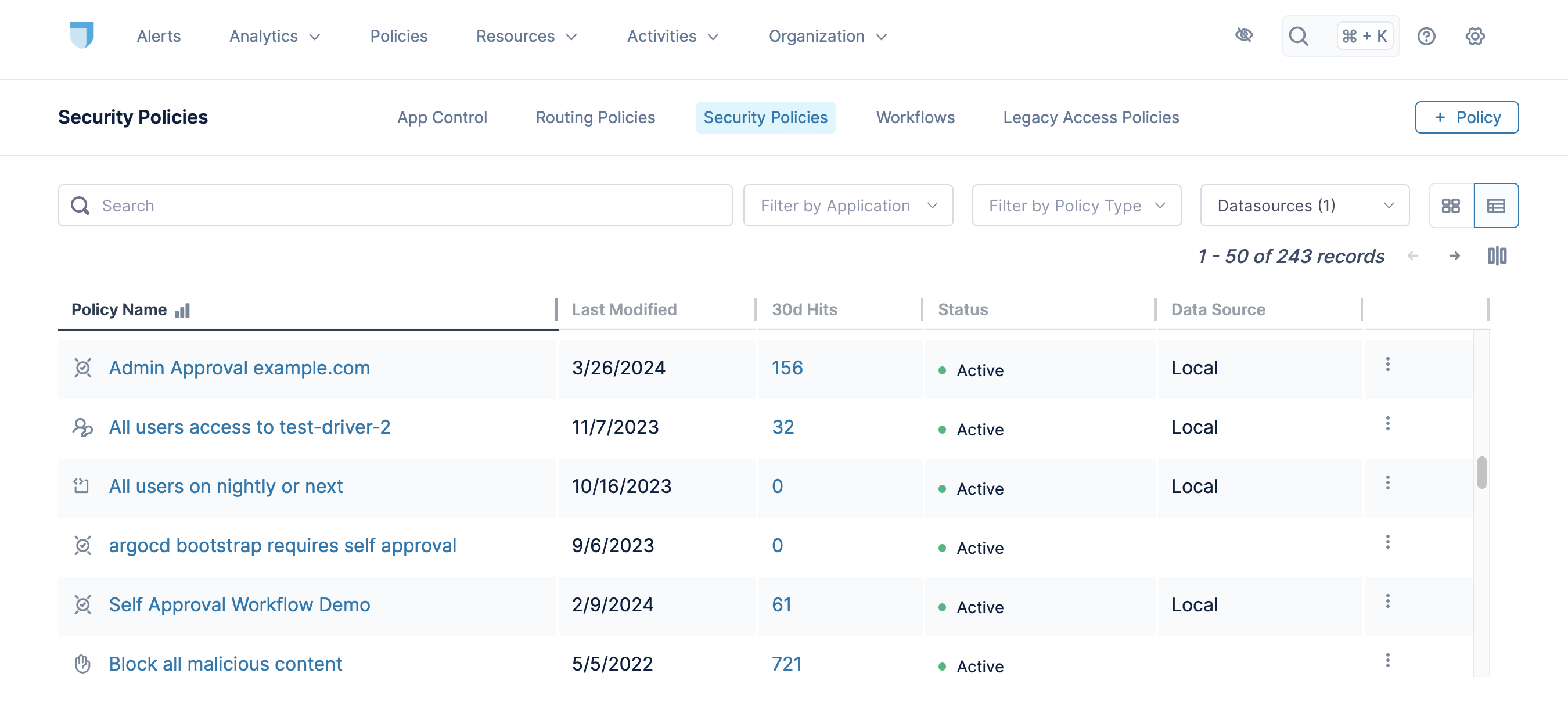
View Security Policies
You can see your existing security policies by clicking Policies > Security Policies. The page displays various information about the policies, such as when it was last updated and its hit count for the last 30 days. The hit count can help you understand how often your users are interacting with the policy.
For the existing policies, you can edit, duplicate, delete, or suspend them using the ⋮ button on each line.
Create a Security Policy
-
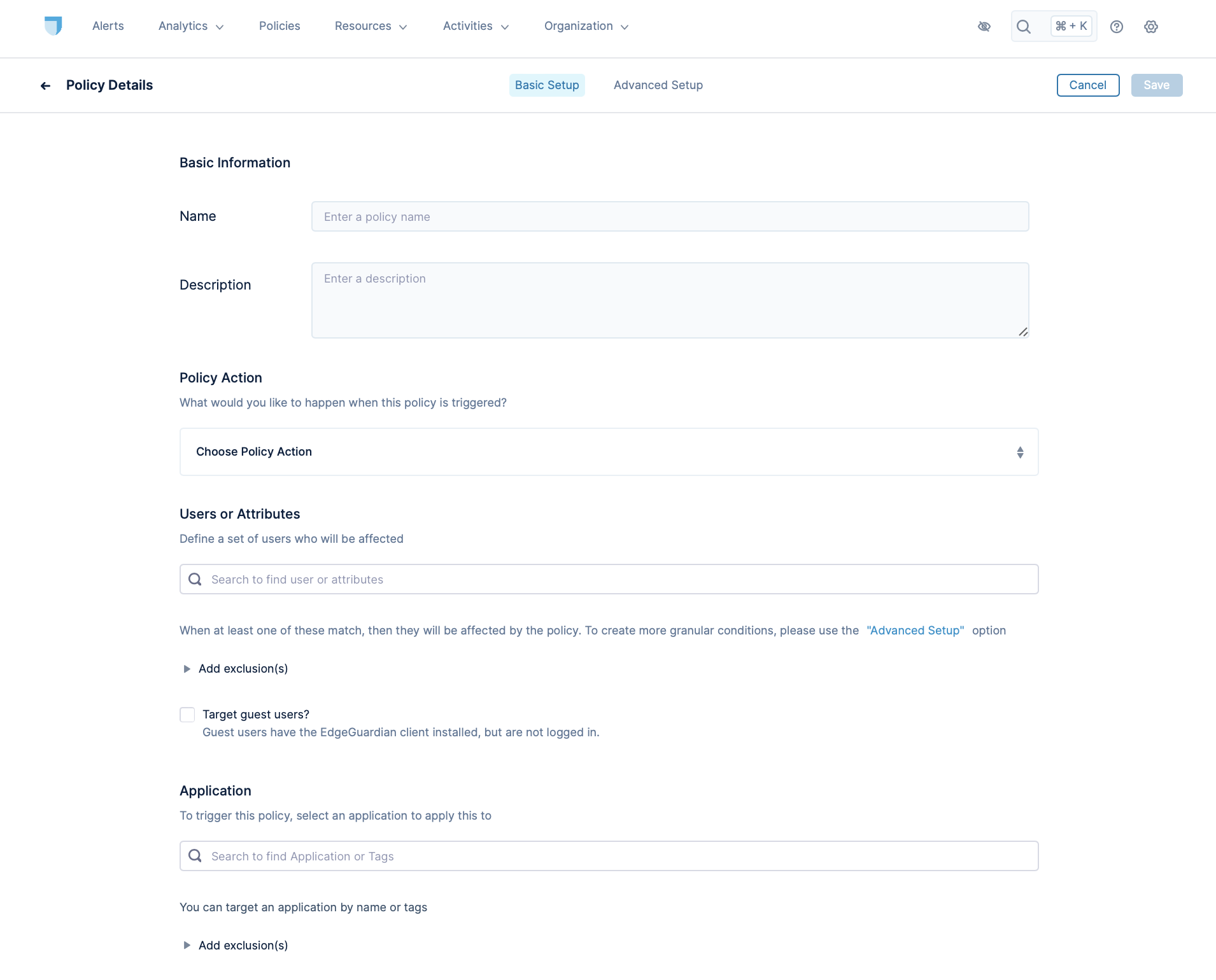
Click on the + Create Policy button at the top right. Lacework Edge will display this screen:
-
Enter a name and descriptions for the policy. For the name, we recommend establishing a naming convention such as "[Policy Type] - [what it affects] - [who it affects]", e.g., "Direct Routing - Streaming Sites - All Users".
-
Choose the action from the options.
-
Specify the users to whom this policy applies. You can choose users by user name, user group or session tag. Session tags apply dynamically assessed criteria to select users, such as the user's location. See Session Tags for more information.
-
Specify any users to be excluded from those who would otherwise be matched by the policy by expanding the Add exclusions area and entering users by user, user group, or tag.
-
If you would like this policy to apply to guest users, select the Target guest users? option.
-
Choose the applications this security policy applies to, by application name or resource tag.
-
Exclude, if desired, individual applications or tags that are otherwise included in your application selection.
-
Click Save.
The new policy should now appear in the security policy list.
Policy Actions
Deny
What it does: Used to deny access to a resource.
When to use: When configuring Internet Security, use this to deny access to malicious sites or certain classifications.
Permit
What it does: Used to allow access to a resource. Equivalent to an Access Policy
When to use: When configuring Internet Security, use this to allow access to trusted sites or certain classifications.
Mitm
What it does: Man-In-The-Middle (MITM) causes Lacework Edge to terminate the TLS connection and impersonate the site, assuming the Client has the Lacework Edge Certificate installed. Lacework Edge checks every request with its security algorithms, instead of just the initial CONNECT request. Lacework Edge also records logs for every request as well, with the full path.
When to use it: Use this to implement content inspection on user traffic.
Run Workflow
What it does: Executes a Workflow for a user. The user will not need to complete the Workflow again when switching between Apps in the same policy.
When to use:
Run App Specific Workflow
What it does: Executes a Workflow for a user. The user will need to complete the Workflow again when switching between Apps in the same Policy.
When to use: