Getting Started
So you're just getting starting with Lacework Edge. First of all, great choice! Lacework Edge brings a wealth of features and intelligence to the task of securing your users and resources.
So what's next? This topic takes you through an end-to-end introduction to its features and the tasks required for setting it up for your environment. It also introduces you to the Lacework Edge console, the primary interface you'll use to set up Lacework Edge and maintain and monitor your deployment. If you're just getting to know Lacework Edge, this topic is a good place to start.
Lacework Edge Console
The Lacework Edge console is the main interface for setting up Lacework Edge and monitoring security in your environment.
Let's take a look at the Lacework Edge console (shrunken for convenience):
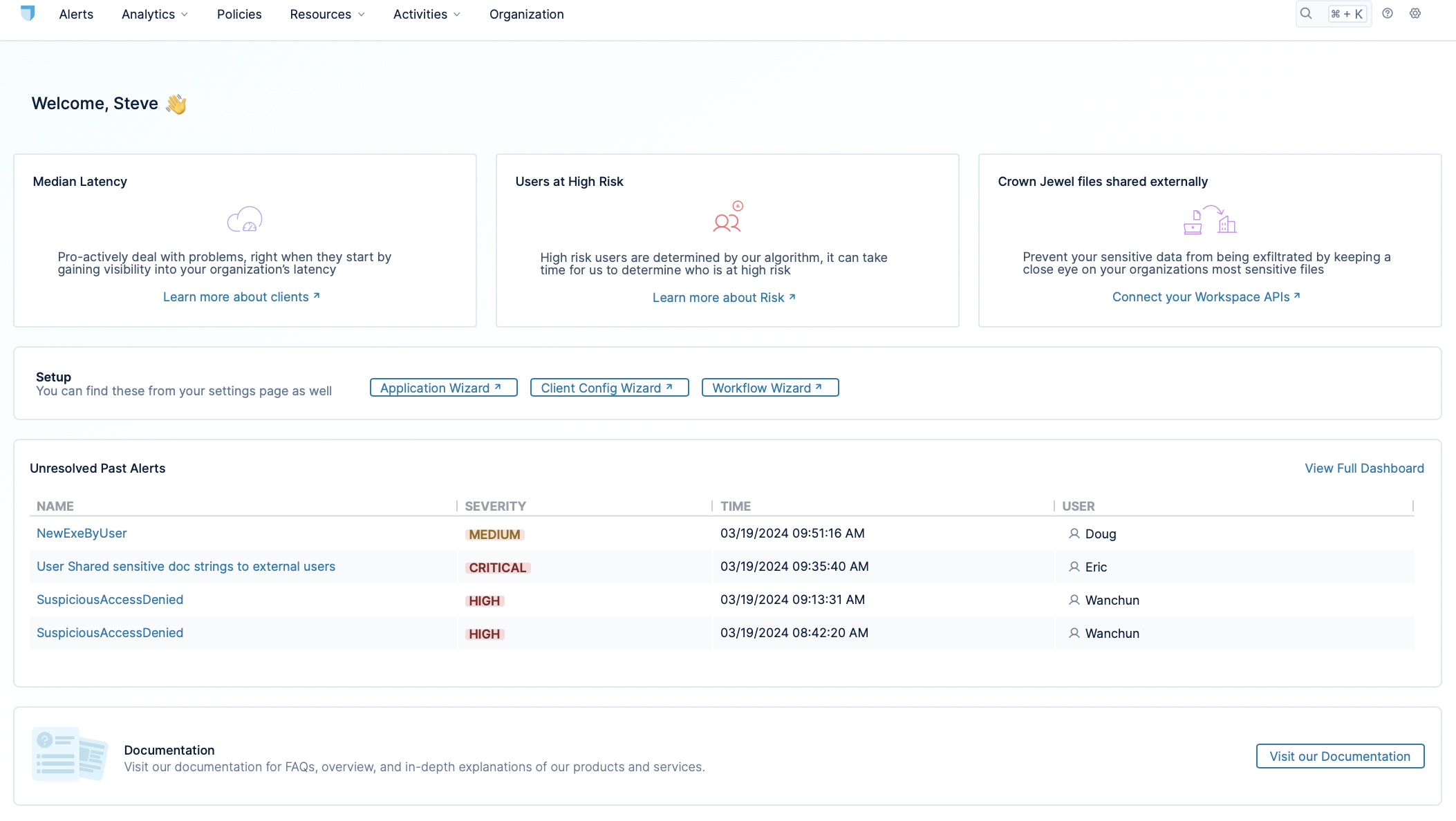
Notice a few important features of the main page. You can use the top menu to navigate to the main pages of the console, such as the analytics dashboard, policies page, and more. The body of the page gives you a quick, heads-up display of the most important information. These include links to unresolved alerts, setup tools, and more.
Guided Setup
The Lacework Edge console includes a built-in guide for setting up Lacework Edge. To open the guided setup, click the setup icon on the right side of the home page.
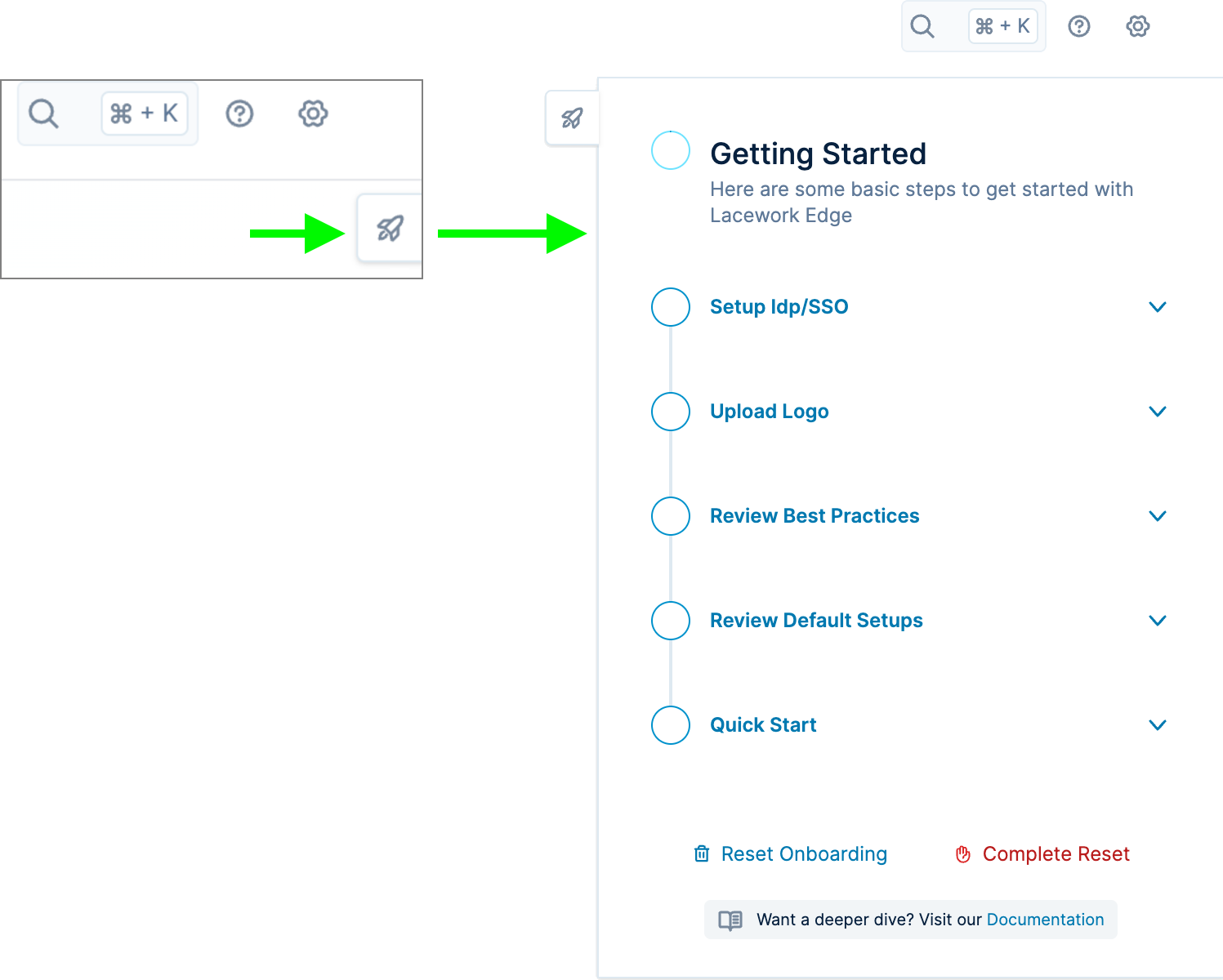
The guide lists the major steps for deploying Lacework Edge, and links to resources where you can learn how to extend your configuration. You can tick off the steps in the guide as you complete them to track and share your progress with other console users. If you leave the console, your progress is retained, so that you can resume the setup later.
Set Up Identity Provider and Single Sign-On
Two important initial steps in deploying Lacework Edge relate to integrating Lacework Edge with your organization's Identity Provider (IdP).
- Once you provide Lacework Edge with API credentials to integrate with your IdP, Edge will bring in your organization's users and user groups, and sync them on a regular basis.
- Once you provide Lacework Edge with SSO metadata from your IdP, Users will be able to use your SSO mechanism to log in to the Edge client, browser extension, or Admin UI.
Lacework Edge supports the following identity providers:
- Google Workspace
- Microsoft Azure AD / Entra ID
- Okta
- OneLogin
- Ping Identity
The instructions for integrating your IdP via API and SSO vary by provider type. For both, you'll need admin access to your IdP's configuration environment.
For more information, see IdP API Integration and SSO/SAML Integration.
Add More Integrations
You can also integrate Lacework Edge with data and document hosting services. This enables you to monitor activity around documentation and data, and detect and prevent misuse or loss of data. Lacework Edge supports the following services:
- Box
- Google Workspace (for Google Drive)
- Snowflake
- Microsoft Office 365
- Salesforce
- GitHub
For more information, see Data Security.
Upload Logo
By configuring your company name and logo in Lacework Edge, you can have your organization's branding integrated into the approval emails and verification workflow pages presented to your users.
Enter your company name and upload the company logo as a PNG file. As noted in the console, the recommended size for the logo is 1024 × 600 and must be less than 200 MB.
Review Best Practices
The best practice review steps pertain to these three primary use cases supported by Lacework Edge:
- Private access security provides secure access to your private applications, both internal and SaaS, from any device and location. It supports legacy apps as a VPN replacement. Once enabled with a workflow you configure, users connect to applications or cloud networks and systems through the Lacework Edge proxy. See Private Access Security for more information.
- Internet security consists of Secure Web Gateway (SWG) capabilities with DNS reputation and malware detection to protect users against Internet risks. These capabilities also enable you to enforce web filtering policies that identify unusual or suspicious activity. After secure Internet access is configured, your users are blocked or warned when they attempt to access malicious or inappropriate sites. See Internet Security for more information.
- Data security enables you to enable documents within commonly used ecosystems, like Microsoft 365, Google Workspace, Dropbox, and more. Lacework Edge can track who has access to what documents and model who should have access to them, ensuring that your sensitive information is kept secure. See Data Security for more information.
Before continuing on, review the documentation and best practices related to these use cases.
Review Default Setups
Policies
Policies are a powerful, flexible mechanism for tailoring Lacework Edge security and privacy for your environment.
A common form of data leak consists of copying/pasting sensitive content to a public website, such as a text storage site like Pastebin. App control policies let you prevent this type of data leak. They control actions in the browser, including copying to the clipboard, pasting from the clipboard, printing, or uploading/downloading files.
Another category of policies in Lacework Edge are security policies. These policies match a condition to an action. Some example actions are to block or allow traffic, route traffic directly to a site, or route through Lacework Edge. Lacework provides several default security policies, and you can create your own.
A policy's action can also be to apply a workflow. Workflows can define a custom login experience to an app, for example, or add an administrator approval step to the login sequence. Deploying Lacework Edge, therefore, involves planning and configuring the workflows you desire and the policies that apply them.
Device Posture
Device posture profiles define the types of devices and device configurations expected for your environment. Device postures allow you to identify unexpected devices, and they also let you manage device security, such as applying updates and security measures.