Content Inspection
How does it work?
When Content Inspection is enabled, the Lacework Edge service will terminate the client's TLS connection and establish a new TLS connection with the destination server. Lacework Edge can then inspect the contents of the TLS connection, and Policies can act on the decrypted traffic. This setup necessitates that Lacework Edge acts as a private certificate authority that the clients must trust.
Instructions
To deploy Content Inspection, you will:
- Create a root CA certificate for your account using the API Client.
- Export the root CA and deploy the above root certificate to your users using an MDM profile. This adds the certificate to the client's list of trusted root CAs.
- Test the policy on a small set of users and/or websites using a Policy and deploy more broadly.
Creating the root CA
Run the following command to create a new root CA certificate. The certificate's public key is returned; the private key is securely stored and is not retrievable.
egcli nervecenter create-ca-certificate
Output:
{
"account_name": "<your account>",
"uuid": "2RXoB1Wz50HRH6hnhYXC31EocNg",
"public_key_pem": "-----BEGIN CERTIFICATE-----\nMIICITCCAcigAwIBAgIMPdwJ23nSQJJc29iAMAoGCCqGSM49BAMCMHMxCzAJBgNV\nBAYTAlVTMUUwEwYDVQQKEwxFZGdlR3VhcmRpYW4wFgYDVQQKEw9qdmltYWwtcHJp\nc3RpbmUwFgYDVQQKEw9qdmltYWwtcHJpc3RpbmUxHTAbBgNVBAMTFEVkZ2VHdWFy\nZGlhbiBSb290IENBMB4XDTIzMDYyMTAzNDcyN1oXDTQzMDYxNzAzNDcyN1owczEL\nMAkGA1UEBhMCVVMxRTATBgNVBAoTDEVkZ2VHdWFyZGlhbjAWBgNVBAoTD2p2aW1h\nbC1wcmlzdGluZTAWBgNVBAoTD2p2aW1hbC1wcmlzdGluZTEdMBsGA1UEAxMURWRn\nZUd1YXJkaWFuIFJvb3QgQ0EwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASEhCxD\n2QolDBeuwZ/w4AR4I9iyzkOvAZkPVwTcQP0U0x91i3fAQtDfLlU8CG93ZFyPqT2W\nvb/So4jwRY2T9Qc8o0IwQDAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB\n/zAdBgNVHQ4EFgQUs7gMmJtZgcWokPN7dwGjzAqLMiAwCgYIKoZIzj0EAwIDRwAw\nRAIgWMX1bkXLo/ZRtRowglZR1zMUf62QWlYl8tw5VdljRGUCIHQTUC7edtWXe06s\n15BnUxaE6kPa7TBDIXGECXSFYveb\n-----END CERTIFICATE-----\n",
"create_time": "1687405647479",
"creator_uuid": "2NO67eb3KyTDGnfkWiLoJ8RfsNj",
"update_time": "1687405647479"
}
Exporting the root CA
To export the certificate to a PEM file, run the following command. You may need to install jq.
egcli nervecenter get-ca-certificate --uuid <uuid from previous step> | jq -r .public_key_pem | tee edgeguardian-root-ca.pem
Output:
-----BEGIN CERTIFICATE-----
MIICITCCAcigAwIBAgIMPdwJ23nSQJJc29iAMAoGCCqGSM49BAMCMHMxCzAJBgNV
BAYTAlVTMUUwEwYDVQQKEwxFZGdlR3VhcmRpYW4wFgYDVQQKEw9qdmltYWwtcHJp
c3RpbmUwFgYDVQQKEw9qdmltYWwtcHJpc3RpbmUxHTAbBgNVBAMTFEVkZ2VHdWFy
ZGlhbiBSb290IENBMB4XDTIzMDYyMTAzNDcyN1oXDTQzMDYxNzAzNDcyN1owczEL
MAkGA1UEBhMCVVMxRTATBgNVBAoTDEVkZ2VHdWFyZGlhbjAWBgNVBAoTD2p2aW1h
bC1wcmlzdGluZTAWBgNVBAoTD2p2aW1hbC1wcmlzdGluZTEdMBsGA1UEAxMURWRn
ZUd1YXJkaWFuIFJvb3QgQ0EwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASEhCxD
2QolDBeuwZ/w4AR4I9iyzkOvAZkPVwTcQP0U0x91i3fAQtDfLlU8CG93ZFyPqT2W
vb/So4jwRY2T9Qc8o0IwQDAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB
/zAdBgNVHQ4EFgQUs7gMmJtZgcWokPN7dwGjzAqLMiAwCgYIKoZIzj0EAwIDRwAw
RAIgWMX1bkXLo/ZRtRowglZR1zMUf62QWlYl8tw5VdljRGUCIHQTUC7edtWXe06s
15BnUxaE6kPa7TBDIXGECXSFYveb
-----END CERTIFICATE-----
MDM profile for deployment
macOS
Download the profile Profile - Root CA Install.
Open the file in a plaintext editor and paste the contents of the certificate
omitting the -----BEGIN CERTIFICATE----- and -----END CERTIFICATE----- lines
into the section that says <!-- CERT GOES HERE -->.
For example:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadCertificateFileName</key>
<string>EdgeGuardianCert</string>
<key>PayloadContent</key>
<data>
MIICITCCAcigAwIBAgIMPdwJ23nSQJJc29iAMAoGCCqGSM49BAMCMHMxCzAJBgNV
BAYTAlVTMUUwEwYDVQQKEwxFZGdlR3VhcmRpYW4wFgYDVQQKEw9qdmltYWwtcHJp
c3RpbmUwFgYDVQQKEw9qdmltYWwtcHJpc3RpbmUxHTAbBgNVBAMTFEVkZ2VHdWFy
ZGlhbiBSb290IENBMB4XDTIzMDYyMTAzNDcyN1oXDTQzMDYxNzAzNDcyN1owczEL
MAkGA1UEBhMCVVMxRTATBgNVBAoTDEVkZ2VHdWFyZGlhbjAWBgNVBAoTD2p2aW1h
bC1wcmlzdGluZTAWBgNVBAoTD2p2aW1hbC1wcmlzdGluZTEdMBsGA1UEAxMURWRn
ZUd1YXJkaWFuIFJvb3QgQ0EwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASEhCxD
2QolDBeuwZ/w4AR4I9iyzkOvAZkPVwTcQP0U0x91i3fAQtDfLlU8CG93ZFyPqT2W
vb/So4jwRY2T9Qc8o0IwQDAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB
/zAdBgNVHQ4EFgQUs7gMmJtZgcWokPN7dwGjzAqLMiAwCgYIKoZIzj0EAwIDRwAw
RAIgWMX1bkXLo/ZRtRowglZR1zMUf62QWlYl8tw5VdljRGUCIHQTUC7edtWXe06s
15BnUxaE6kPa7TBDIXGECXSFYveb
</data>
<key>PayloadDescription</key>
<string>Adds Certificate Root for EdgeGuardian</string>
<key>PayloadDisplayName</key>
<string>EdgeGuaridan Root Cert</string>
<key>PayloadIdentifier</key>
<string>com.edgeguard.cert.23a4f749-1d2f-46b1-a2fc-9db8ad283e7a</string>
<key>PayloadType</key>
<string>com.apple.security.root</string>
<key>PayloadUUID</key>
<string>23a4f749-1d2f-46b1-a2fc-9db8ad283e7a</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</array>
<key>PayloadDisplayName</key>
<string>EdgeGuardian Root Cert</string>
<key>PayloadIdentifier</key>
<string>com.edgeguard.5da368d4-cb97-416c-ae99-ff1a78b078eb</string>
<key>PayloadRemovalDisallowed</key>
<false/>
<key>PayloadScope</key>
<string>User</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>5da368d4-cb97-416c-ae99-ff1a78b078eb</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
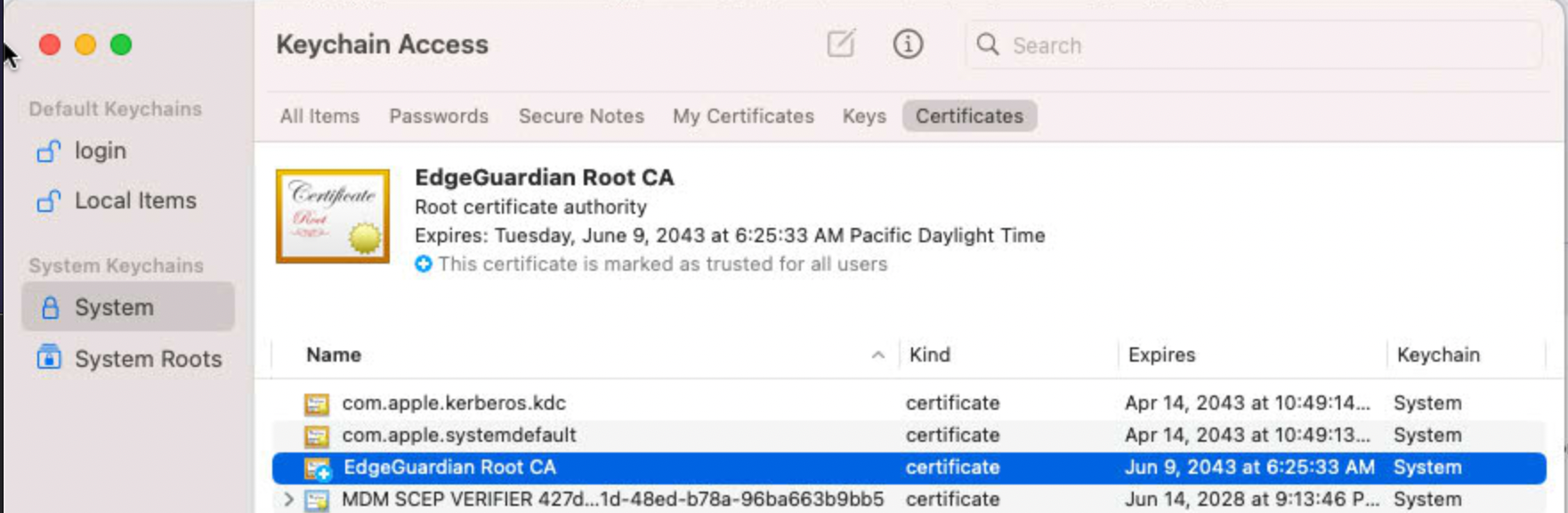
Once you deploy the profile, you should verify that the certificate has been marked as trusted. Open "KeyChain Access", navigate to "System Roots" and you should see a certificate named "EdgeGuardian Root CA" as follows:
Windows
TBD.
Enabling the root CA
Once the certificate has been deployed to all clients, you will need to mark the certificate as ACTIVE.
egcli nervecenter update-ca-certificate --uuid 2RXoB1Wz50HRH6hnhYXC31EocNg --status ACTIVE
Output:
{
"account_name": "<your account here>",
"uuid": "2RXoB1Wz50HRH6hnhYXC31EocNg",
"status": "ACTIVE",
"public_key_pem": "-----BEGIN CERTIFICATE-----\nMIICITCCAcigAwIBAgIMPdwJ23nSQJJc29iAMAoGCCqGSM49BAMCMHMxCzAJBgNV\nBAYTAlVTMUUwEwYDVQQKEwxFZGdlR3VhcmRpYW4wFgYDVQQKEw9qdmltYWwtcHJp\nc3RpbmUwFgYDVQQKEw9qdmltYWwtcHJpc3RpbmUxHTAbBgNVBAMTFEVkZ2VHdWFy\nZGlhbiBSb290IENBMB4XDTIzMDYyMTAzNDcyN1oXDTQzMDYxNzAzNDcyN1owczEL\nMAkGA1UEBhMCVVMxRTATBgNVBAoTDEVkZ2VHdWFyZGlhbjAWBgNVBAoTD2p2aW1h\nbC1wcmlzdGluZTAWBgNVBAoTD2p2aW1hbC1wcmlzdGluZTEdMBsGA1UEAxMURWRn\nZUd1YXJkaWFuIFJvb3QgQ0EwWTATBgcqhkjOPQIBBggqhkjOPQMBBwNCAASEhCxD\n2QolDBeuwZ/w4AR4I9iyzkOvAZkPVwTcQP0U0x91i3fAQtDfLlU8CG93ZFyPqT2W\nvb/So4jwRY2T9Qc8o0IwQDAOBgNVHQ8BAf8EBAMCAQYwDwYDVR0TAQH/BAUwAwEB\n/zAdBgNVHQ4EFgQUs7gMmJtZgcWokPN7dwGjzAqLMiAwCgYIKoZIzj0EAwIDRwAw\nRAIgWMX1bkXLo/ZRtRowglZR1zMUf62QWlYl8tw5VdljRGUCIHQTUC7edtWXe06s\n15BnUxaE6kPa7TBDIXGECXSFYveb\n-----END CERTIFICATE-----\n",
"create_time": "1687405647479",
"creator_uuid": "2NO67eb3KyTDGnfkWiLoJ8RfsNj",
"updater_uuid": "2NO67eb3KyTDGnfkWiLoJ8RfsNj",
"update_time": "1687407967486"
}
You may create multiple certificates, and any number of certificates might be
active at any point in time. However, only the latest created certificate
(created_at field) will be used as the root CA.
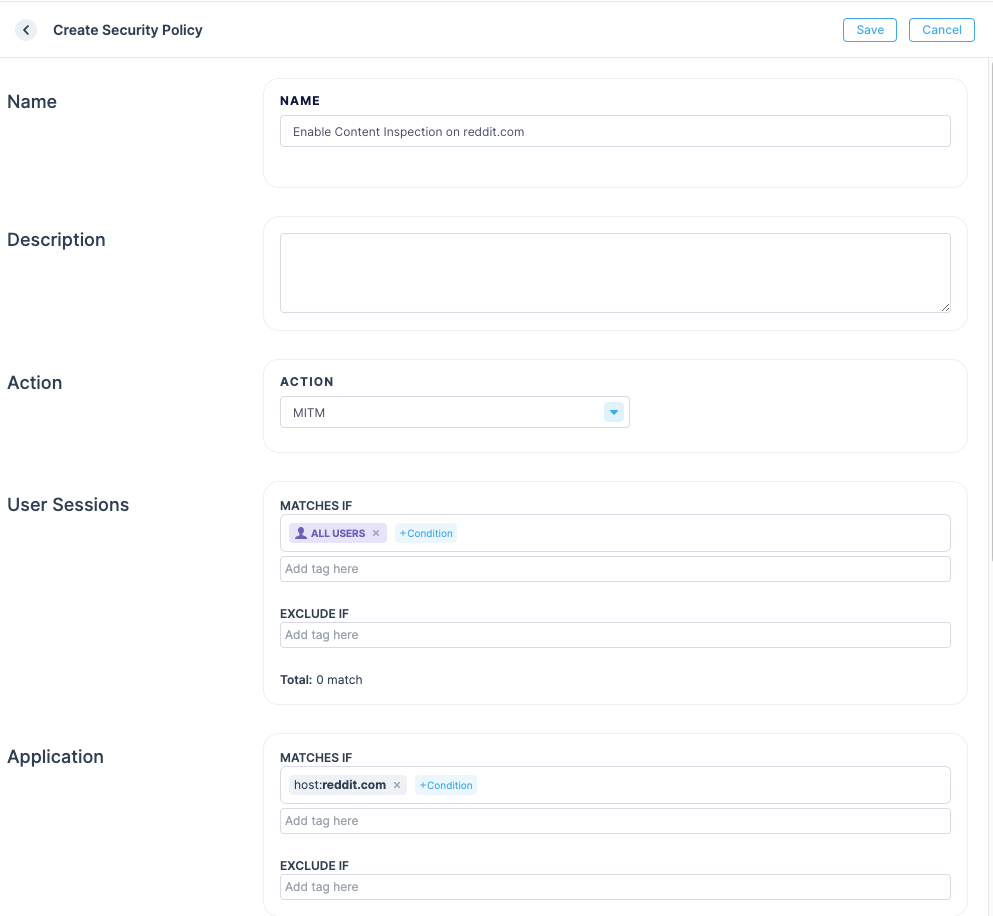
Testing content inspection
You can enable content inspection for specific set of users using a Security Policy with the MITM action. If the root CA was not installed and marked as trusted, the user may see a certificate warning.
Here is an example policy that enables Content Inspection for all users and a specific host.
Once enabled, if you visit the URL and inspect the certificate chain, you should see the following:
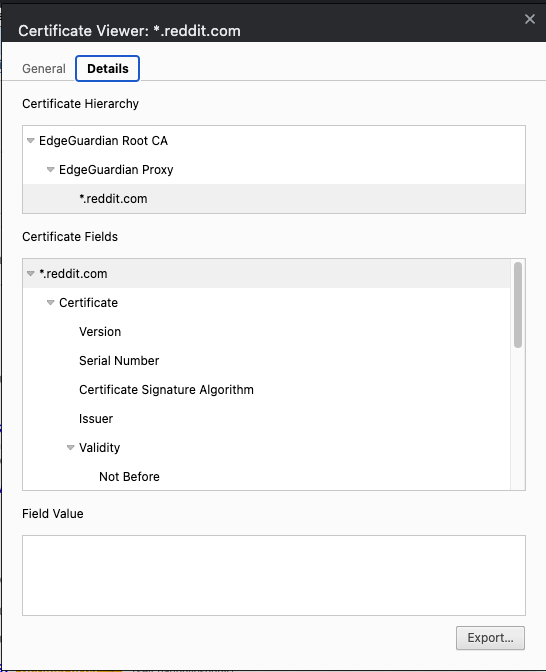
The chain of trust is as follows:
-
The leaf certificate is for
*.reddit.com. This matches the certificate thatreddit.comwould have served without any content inspection in place. -
The "EdgeGuardian Proxy" intermediate certificate: This certificate uniquely identifies the particular gateway the client is connected to. This intermediate certificate is short-lived (one day validity).
When users connect to our gateway, our gateway automatically creates a temporary, intermediate CA certificate, and issues a certificate signing request to a secure, centralized service. The centralized service signs the certificate signing request with the trusted root CA that you created and limits the certificate's validity to one day.
This design ensures that the private key for the root CA that is marked trusted on your users' devices is securely stored and is never distributed across all our gateway points of presence.
-
The "EdgeGuardian Root CA" root CA that is marked as trusted on your users' devices.
Best practices
Notes
Lacework Edge supports all versions of TLS, except for TLS1.3 clients that
encrypt the ClientHello using eSNI or ECH. Most TLS1.3 clients do not use this
feature. Lacework Edge only supports http/1.1 and h2 (http/2) ALPNs
negotiated between the client and server, and it preserves the client's choice;
notably, it does not downgrade h2-compatible clients to http/1.1.
If traffic matches the MITM Policy but is not HTTPS, Lacework Edge skips
the content inspection checks. Thus, it is safe to enable a MITM policy for
github.com even if your users use ssh to access git.
Content Inspection policy only applies to traffic that is routed via Lacework Edge.