User Risk
User behavior presents a significant source of potential security risk for organizations. This risk may come from internal users, acting intentionally or unintentionally, or from external actors having gained access to an internal account.
Lacework Edge provides visibility into user behavior so that you can recognize and safeguard against common types of user risk.
Lacework Edge detects certain user actions or behaviors that can contribute to risk and classifies them as risk factors. Some examples of these behaviors are: a user who unexpectedly connects from an unusual geographic location, a user who disables their device activation lock, or a user who suddenly shares a large number of documents with external users.
The User Risk insights page displays the risk factors, along with metrics that reflect recent incidents associated with those factors:
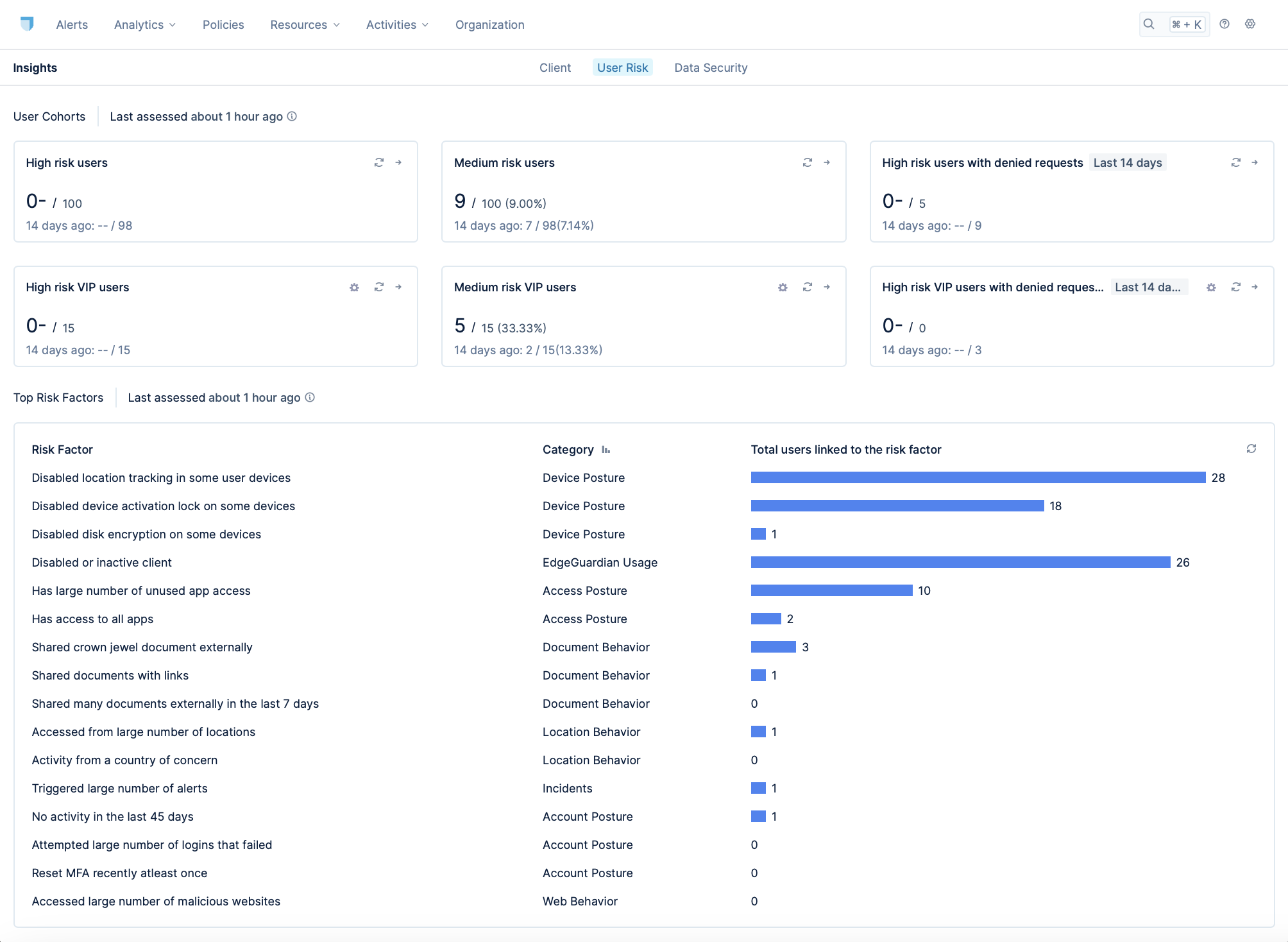
As shown, Lacework Edge displays the number of incidences associated with the risk factors across various types of user cohorts.
One of those cohorts is user risk level, which categorizes users as low, medium, or high risk. By establishing a baseline of expected behavior and assessing risk continuously, Lacework Edge can trigger changes to the user's risk level based on the user's actions. Furthermore, you can define policies that apply workflows that are automatically applied when the user's risk level changes.
For example, consider James, a user with a low risk level. As such, he can access the company's sensitive applications like Jira and GitHub with the company's usual SSO login mechanism. Say, however, that James does something that triggers a change to his risk profile, such as attempting to install an unsanctioned application on his device. This may raise James' risk level to high. Such a change would make James subject to policies that are applicable to high risk users, which can trigger workflows with heightened security measures. For example, one such workflow might require high risk users like James to have administrative approval while attempting to access Jira or GitHub.
In this way, Lacework Edge enhances the security of your environment by defining and detecting common user risk patterns and enabling you to immediately adapt the risk exposure in your environment based on realtime events.