Architecture
Lacework Edge transforms secure access with its state-of-the-art, Zero Trust-based architecture. Within the architecture, all users and devices — including workstations, laptops, users with browser extensions, mobile clients, and more — must connect within the proxy-based Edge solution. Edge then exclusively facilitates secure access to private applications, web applications, SaaS apps, and other resources.
Private applications establish outbound connections with the Lacework Edge Connector instance that is close to the application, facilitating the connection between the application and Lacework Edge. Subsequently, Lacework Edge brokers the connection between the user requesting an application and the application itself. It then enforces access controls and maintains a high level of security throughout the connectivity.
Overview
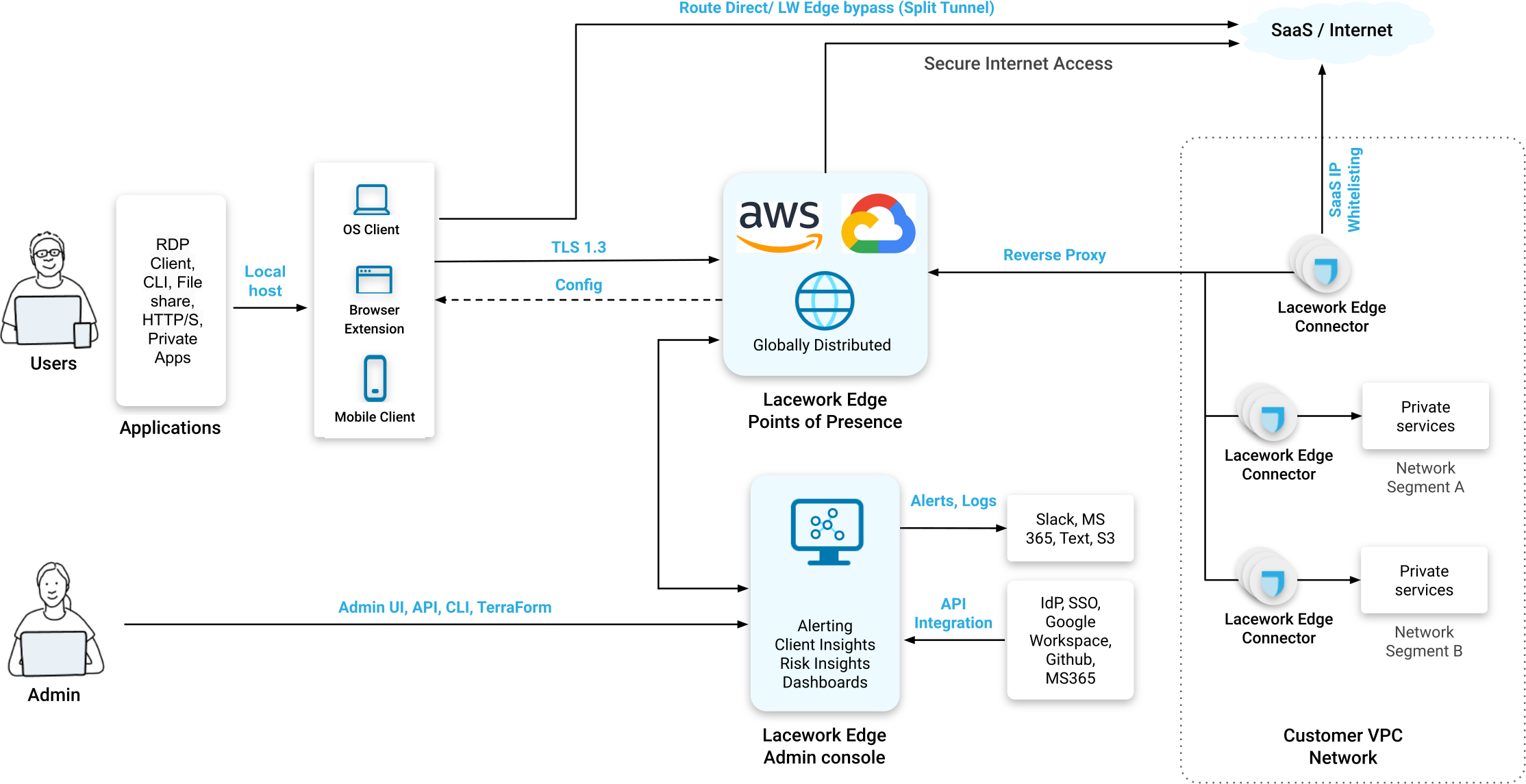
Connectors
Software running within your network that communicates with the Lacework Edge SaaS to broker connectivity to private resources.
Learn more about Connectors and Connector deployment here.
Clients
Software running on your end-user's desktop that connects to the Lacework Edge SaaS-based point of presence to route traffic through EdgeGuard, providing security of and access to resources protected by Lacework Edge.
Learn more about Clients and Client deployment here.
Lacework Edge Gateways / PoPs
Services running in multiple cloud regions, to which your clients will connect and arbitrate access to your internal and cloud resources.
Lacework Edge Control Plane / Admin Interfaces (UI, CLI, API)
Services running in multiple cloud regions (customers are assigned to one region for Admin), to which customers connect in order to administer their Lacework Edge environment and analyze incoming data about client activity, collected from both the clients and 3rd party services. This is configured at the time of account creation by Lacework Edge and can not be changed.
Learn more about Admin Interfaces here.
Connecting as a User
Lacework Edge offers a range of deployment options to provide secure access to all users and devices.
- Client applications: recommended for sanctioned devices for workstations and mobile devices
- Browser extensions: recommended for sanctioned devices and contractors using their own devices (BYODs)
- Clientless access: SSO-enforced and leverages reverse proxy for unsanctioned devices and provides broader access to specific resources
Lacework Edge operates on a global scale by utilizing distributed proxies, known as points of presence (PoPs), deployed in multiple cloud environments like Amazon Web Services (AWS) and Google Cloud. These PoPs maintain consistent configurations and setups across the platform.
When clients initiate a connection, the intelligent client application automatically selects the most suitable PoP based on proximity. Each PoP hosts a rule-based engine that evaluates incoming traffic against predefined rules. After connecting to the PoP, the users traverse the highly performant networks of the cloud service provider (CSP) to their destination.
Connecting as an Administrator
Administrators connect to the centralized SaaS-hosted Lacework Edge solution to perform administrative and investigative functions. Lacework Edge offers multiple interfaces to its control plane — UI, API, CLI, and Terraform Provider. While the CLI and API are solely used for configuration, the UI provides additional visual functionality for administrators and analysts, including activity views, alert investigations, curated insights, and customizable dashboards.
Lacework Edge’s application wizard is designed for administrators and streamlines the onboarding of apps to just a few clicks. By utilizing Terraform, the entire process of establishing connectivity to an app, implementing access rules, and enforcing security policies can be automated alongside the deployment of the app. Lacework Edge offers a guide to walk administrators through these setup and configuration tasks.