Lacework Edge Connectors
The Lacework Edge connector is an agent that runs inside your networks that dials into Lacework Edge and provides connectivity into that network. Deploying and administering connectors is an important part of implementing security for your environment. Lacework provides tools that make it easier to deploy connectors to your cloud and on-premises environments.
All deployments first require you to create a connector token, which you will configure in the connector that you deploy. Ideally, connectors should be deployed as a cluster or pair, which provides load balancing and fault tolerance. You join multiple connectors into a single cluster by installing the same connector token in each connector that you want to be part of the cluster.
Considerations
The following considerations apply to connector deployment:
- If using Lacework Edge to replace an existing VPN server to arbitrate access to on-premise resources, run the connector with the same networking and permissions as existing VPN servers, ideally in VMs next to them.
- For granting access to cloud-based private resources, the Connector will need to either reside in the same subnets as those resources, or in a peered VPC, such that it can access them.
- There is no limit to the number of connectors you can deploy, aside from the cost of the compute resources for each connector.
- For high-availability and high-performance, we recommend deploying connectors in a cluster.
- If using the single-deployment options (OVA, package deployments), we recommend running at least two instances of the connector in the same VPC. Connectors deployed with the same token will be grouped together as multiple instances of the same connector.
Deployment options
- For AWS deployments, a CloudFormation template is available for deploying connectors into AWS Fargate compute engine in a cluster of configurable size.
- For Azure deployments, an Azure Resource Manager (ARM) template is available for deploying connectors as Virtual Machines.
- For deployment to a Kubernetes cluster, a Helm chart is available. This helm chart can be used with both on-premises and cloud Kubernetes environments (for example, GKE).
- For a VM-level deployment, a complete VM (OVA) image, Linux and Windows packages are available.
Using a Connector for SaaS Access
In order to secure publicly-accessible services, you can use a Connector in concert with that service's network access control capabilities. Cloud providers such as AWS, Azure and GCP, and popular services like GitHub, SalesForce and Snowflake all support limiting access to IPs and IP ranges.
- Deploy a connector (or cluster of connectors) with a static public IP or with a NAT gateway that has a static public IP.
- Create Apps in Lacework Edge for your SaaS services, choosing that connector for the "Route Via Connector" option.
- Set up your SaaS service to restrict access to the public/NAT IP of your connector (see links above for common examples of how to do this).
Connector Deployment
These steps apply to all connectors for all supported environments.
Step 1: Create a Connector in the Console
- Go to Resources > Connectors in the console.
- Click + Connector.
- Provide a name of the connector and optionally, a display name. If provided, the Display Name value appears as the name for the connector in the list of connectors in the console.
- Copy the token that is generated and save it. Once the connector is created you will see it in a state labeled "Initialized".
Step 2: Deploy the Connector
With your token in hand, follow the instructions in the following documents to deploy a connector appropriate for your intended environment:
- AWS CloudFormation Deployment
- Azure Template Deployment
- Kubernetes Deployment
- Linux Package Deployment
- Virtual Machine Deployment
- Windows Package Deployment
Step 3: Verify Connector State
- After deploying the connector, go to Inventory > Connectors in the console and verify that the connector appears in the Active state.
- If you have deployed multiple instances using the same connector token, they appear as instances under the same connector.
Connector Clustering
For high-availability and high-performance, we recommend deploying connectors in a cluster.
All that is required to cluster connectors is that each connector instance has the same network access - the applications you will be connecting users to through these connector should all be reachable and their domain names resolvable as is applicable.
To deploy connectors as a cluster, simply use the same connector token for each instance that is to be part of the cluster. Once your connector instances connect to the Lacework Edge proxies, they will be represented as instances of the same connector in the Admin UI, like so:
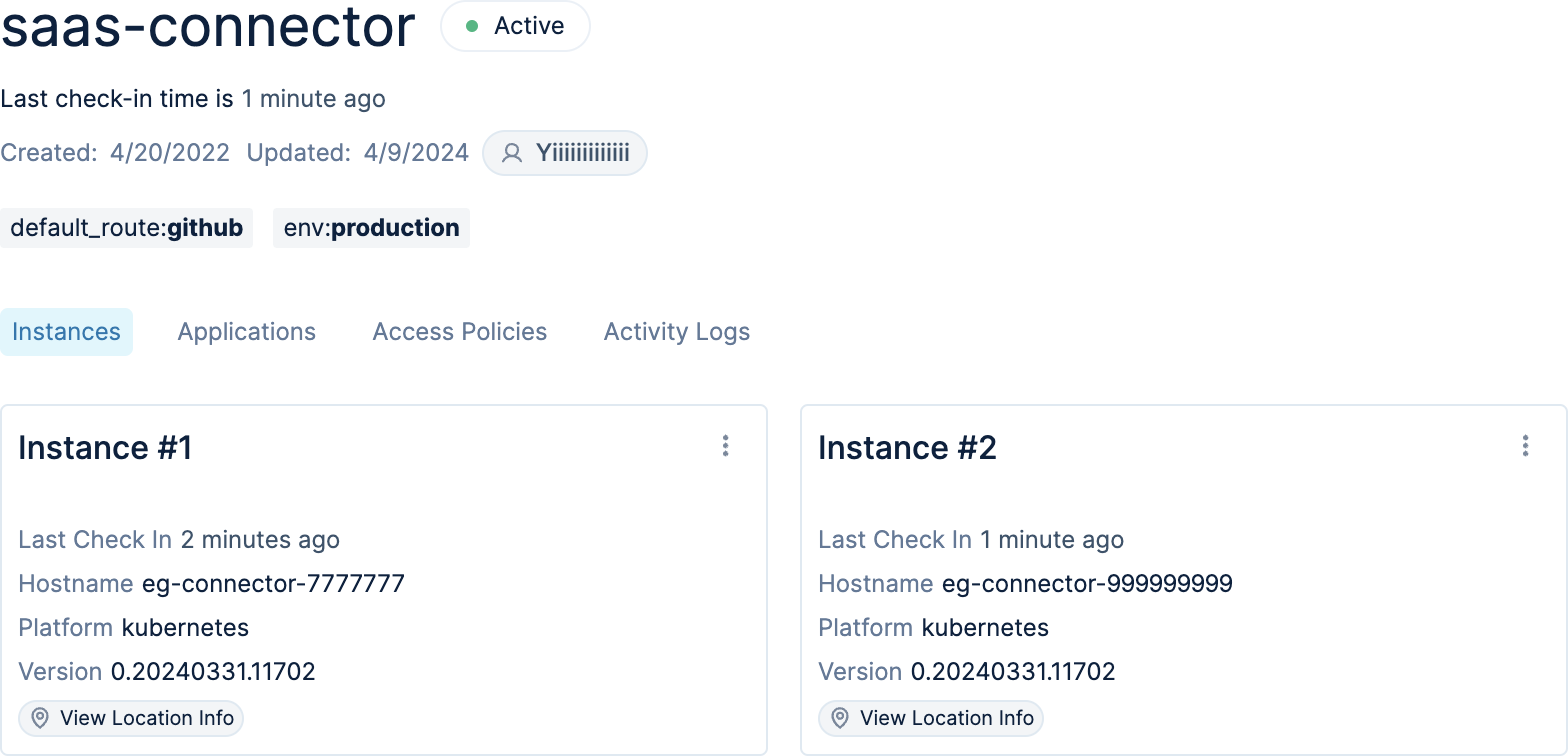
Once clustered, connectors will service requests in a simple round-robin order. If one of those connectors was to stop reporting, traffic would failover to the remaining connectors.