Lists
Lists are collections of user data which may be used for many functions. A list may be pertinent to modeling, data visualization, and data analytics. Lacework Edge commonly uses list for
- Organization settings (can sometimes be simple variables);
- Maintainable multi-use grouping of data;
- Intelligences.
Lists are displayed as cards, as shown in the following screenshot:
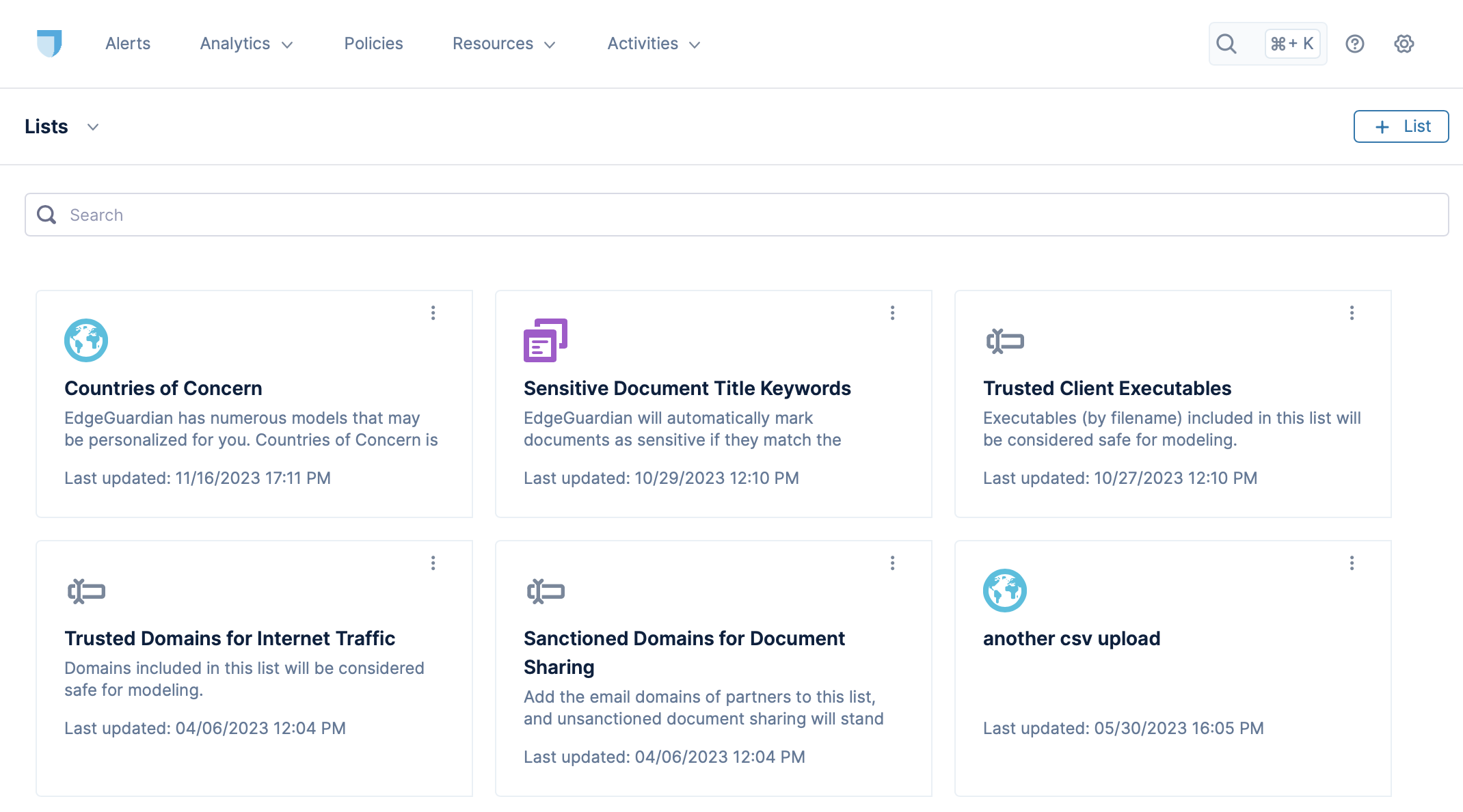
Click on a list to see its details.
Built-in Lists
Countries of concern
Countries of Concern contains the countries used in the Activity from a country of concern user risk
While there are no “bad” countries, there are some that might be odd for a user session, or even to send your company data.
You can modify the list of countries of concern, and Lacework Edge's models will do the rest. (List based from https://www.state.gov/countries-of-particular-concern-special-watch-list-countries-entities-of-particular-concern/#CountriesofParticularConcern)
Trusted Domains for Internet Traffic
Domains included in this list will be considered safe for modeling.
Trusted Client Executables
Executables (by filename) included in this list will be considered safe for modeling.
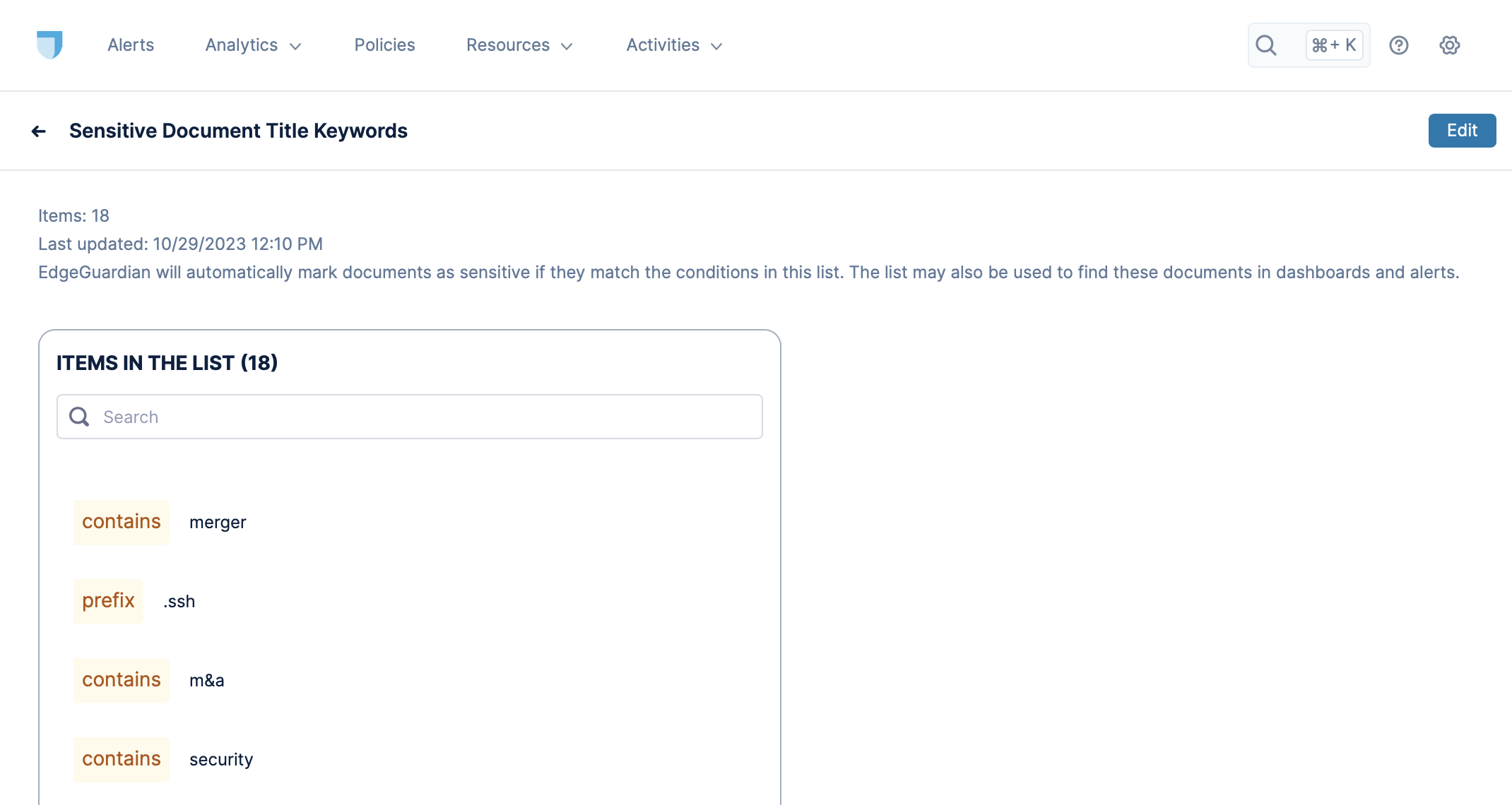
Sensitive Document Title Keywords
Lacework Edge will automatically mark documents as sensitive if they match the conditions in this list. The list may also be used to find these documents in dashboards and alerts.
Sanctioned Domains for Document Sharing
Add the email domains of partners to this list, and unsanctioned document sharing will stand out in the Data Security dashboard.
Crown Jewel Documents
These documents are marked as particularly sensitive so that suspicious activity stands out. Add to this list from the document directory.
This list is empty by default.
Sanctioned OAuth Apps
Add the Application name of applications approved to use OAuth to this list, and unsanctioned App usage will stand out in the OAuth Insights dashboard.
VIP Users
Designate users/groups as VIPs and pivot to their security risk insights.
Custom Lists
You can create your own lists and use them in various scenarios.
- Go to Resources > Lists.
- Click the add list button.
- Provide a name for the list and description.
- Click Save
- Click on your list.
- Edit the list, adding the values in the list. For each value, specify the match criteria for the string.
For instance, if you create a documents list and add a prefix of "int_", it will match any document that starts with "int_".
Choose from these types:
- Generic
- Exact
- Prefix
- Suffix
- contains
- Domains
- Exact
- Prefix
- Suffix
- contains
- Documents
- Exact
- Prefix
- Suffix
- contains
- Generic